
Kernel-mode Hardware-enforced Stack Protection is a security feature introduced in Windows 11 22H2 that protects systems from various memory attacks, such as stack buffer overflows.
Microsoft added this feature to Windows 11 22H2 as part of a Microsoft Defender update in April 2023.
When enabled, Kernel-mode Hardware-enforced Stack Protection will enhance the security of Windows by using hardware to enforce stack protection, making it more difficult for attackers to exploit vulnerabilities.
What is Kernel-mode Hardware-enforced Stack Protection?
Windows Kernel-mode Hardware-enforced Stack Protection is a security feature that primarily protects against stack buffer overflow attacks, where an attacker attempts to trigger arbitrary code execution by overflowing a buffer (temporary memory storage) on the stack (a data structure used to store a program's function calls and local variables).
During these attacks, the attacker attempts to overwrite the return address or control data to redirect the execution of a program to run malicious code of the attacker's choosing.
The technique of overwriting the return address or control data to redirect a program's execution flow is known as a Return-Oriented Programming (ROP) attack.
The Windows Kernel-mode Hardware-enforced Stack Protection feature requires a special hardware-based temporary stack called Shadow Stacks to work.
A Shadow Stack is a temporary memory stack that mirrors the standard stack used by the operating system, and the stack cannot be modified by applications running in Windows.
These Shadow Stacks are used in the following way:
- When a program's function is called, the return address is stored in both the normal stack and the Shadow Stack.
- When the function returns, the Hardware-enforced Stack Protection feature checks if the return address from the primary stack matches the one stored on the Shadow Stack.
- If the return addresses match, the function returns as expected, and the program execution continues normally.
- However, if the return addresses do not match, this could indicate an attack, such as a stack buffer overflow or an ROP attack. When this happens, Windows will terminate the process to prevent the execution of malicious code.
Using Shadow Stacks, Hardware-enforced Stack Protection feature can mitigate attacks, thus protecting the system from vulnerabilities, including zero-days.
However, as Shadow Stacks require Intel's Control-Flow Enforcement Technology (CET) technology, the feature is only available on newer CPUs.
Therefore, to use the Windows Kernel-mode Hardware-enforced Stack Protection, a device must have an Intel Tiger Lake CPU or AMD Zen3 CPU and later with CPU virtualization enabled in the BIOS.
How to enable Kernel-mode Hardware-enforced Stack Protection
While the Windows Kernel-mode Hardware-enforced Stack Protection feature can be complicated to understand, enabling the feature is fairly easy.
If you are running Windows 11 22H2 with the latest updates, open Windows Security and go into Device Security > Core Isolation.
If you have the required hardware and CPU virtualization is enabled, you will see a setting called 'Kernel-mode Hardware-enforced Stack Protection,' as shown below.
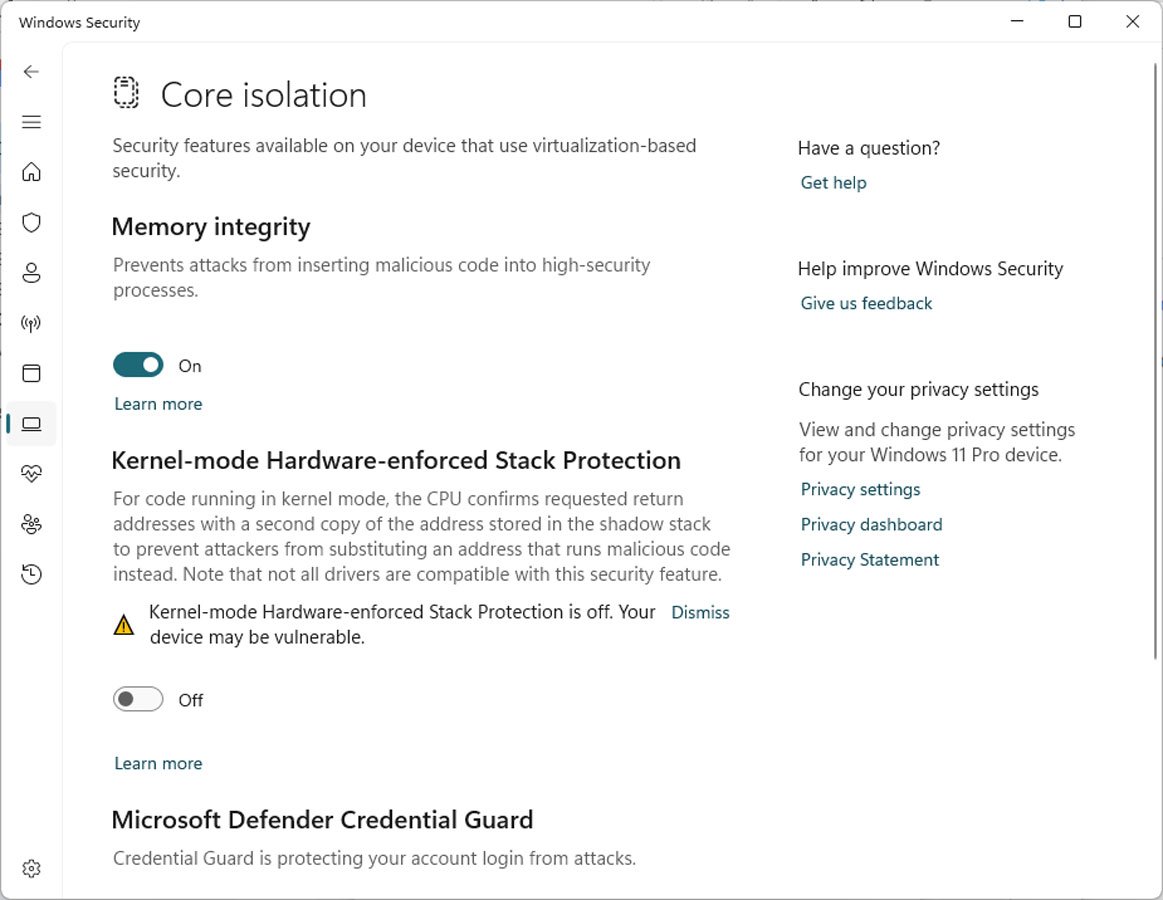
Source: BleepingComputer
To enable the feature, simply toggle it to 'On', and Windows will check the loaded device drivers to see if there are any that could conflict with the security feature.
If any conflicting drivers are detected, it will prompt you to review the list of drivers to update to newer versions before you can enable the feature.
Once you update the drivers to the latest versions, you can attempt to enable the feature again and see if there are any further conflicts.
If no conflicting drivers are found, Windows may prompt you to restart the computer to enable the feature.
May cause unexpected behavior
Unfortunately, when this feature is enabled, you may find that specific programs no longer work as their drivers conflict with the Kernel-mode Hardware-enforced Stack Protection feature.
This commonly happens when Windows is unaware of a driver that conflicts with the feature and allows it to be enabled anyway.
While these conflicts could cause Windows to crash, it is more common that the program will no longer launch, and Windows will state the driver is incompatible and prompt you to disable the security feature.
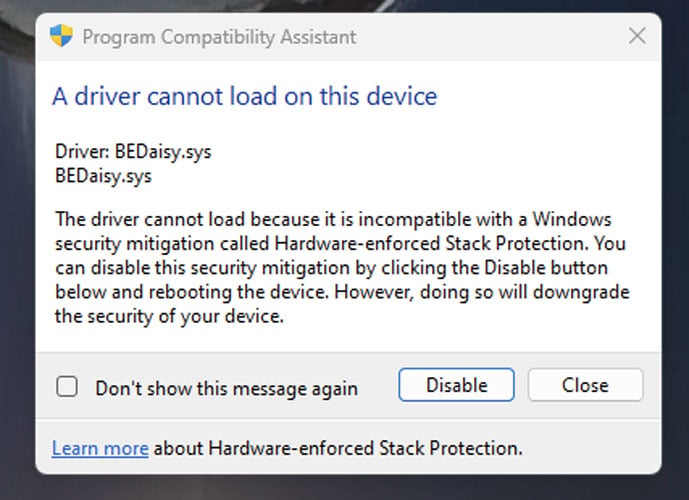
Source: Reddit
Users who have enabled this feature report that many of the conflicts are with copyright protection and anti-cheat drivers used by games, including PUBG, Valorant (Riot Vanguard), Bloodhunt, Destiny 2, Genshin Impact, Phantasy Star Online 2 (Game Guard) and Dayz.
However, as more users begin to use this Windows security feature, we will likely see upgraded versions of these anti-cheat and copyright protection programs to support stack protection.
from Computer Tutorials and How-Tos https://ift.tt/SaB3qkg
via IFTTT













No comments:
Post a Comment